What’s New with IntelliMagic Vision for z/OS? 2024.1
This month we’re introducing updates to the Subsystem Topology Viewer, new Long-term MSU/MIPS Reporting, updates to ZPARM settings and Average Line Configurations, as well as updates to TCP/IP Communications reports.
Let’s dive right into these changes:
Subsystem Topology Reports
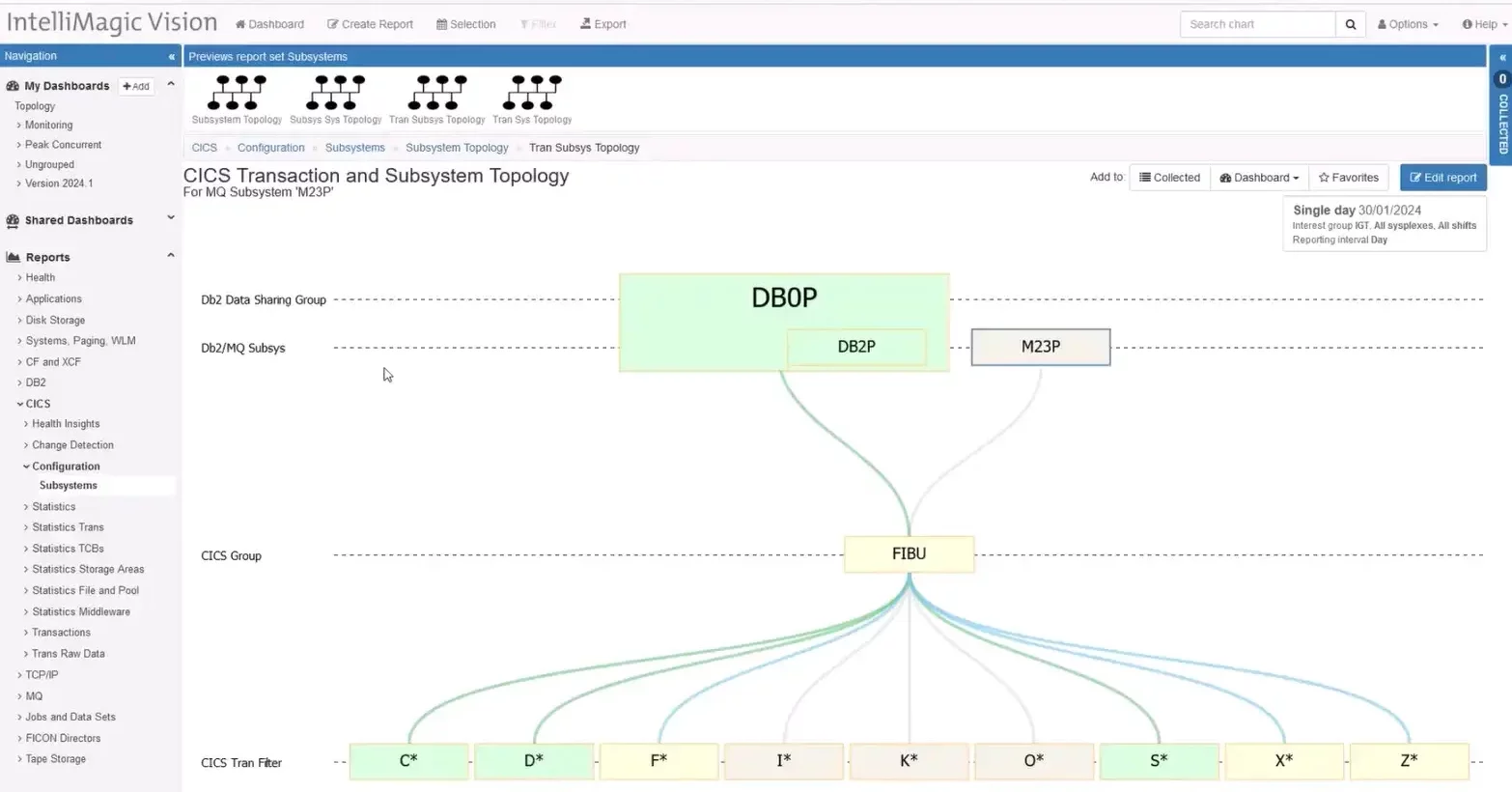
IntelliMagic Vision 2024.01 introduces major updates to the Subsystem Topology Viewer, offering enhanced insights into the interactions between CICS, Db2, and MQ.
With the inclusion of CICS Transaction IDs in reports, users can now identify the specific transactions linked to Db2 Data Sharing Groups and MQ queue managers. Drilldowns to CICS Regions are also available, enabling a comprehensive understanding of system dynamics. Whether troubleshooting issues with an MQ subsystem or exploring dependencies on Db2 Data Sharing Groups, the Subsystem Topology reports provide invaluable insights.
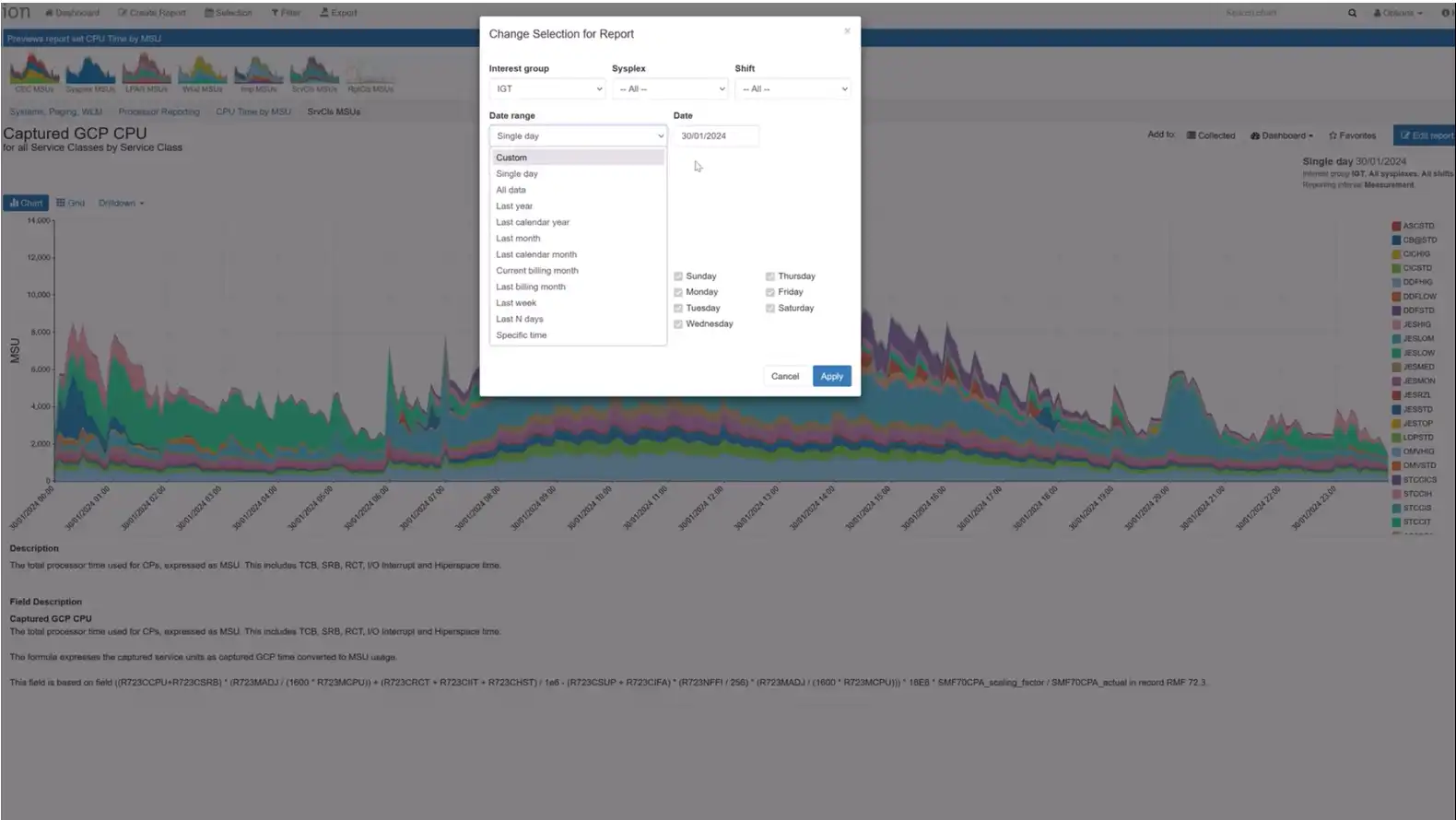
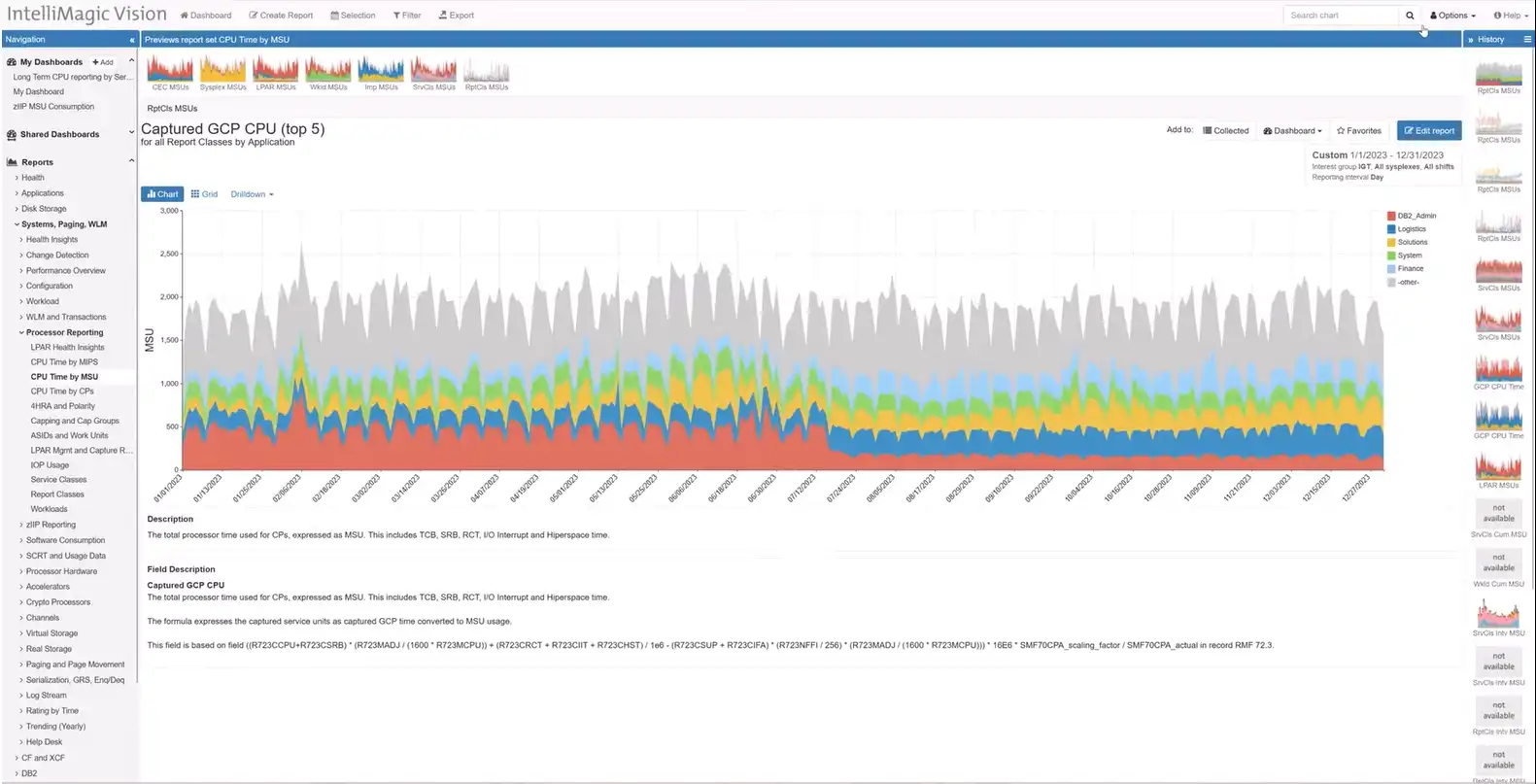
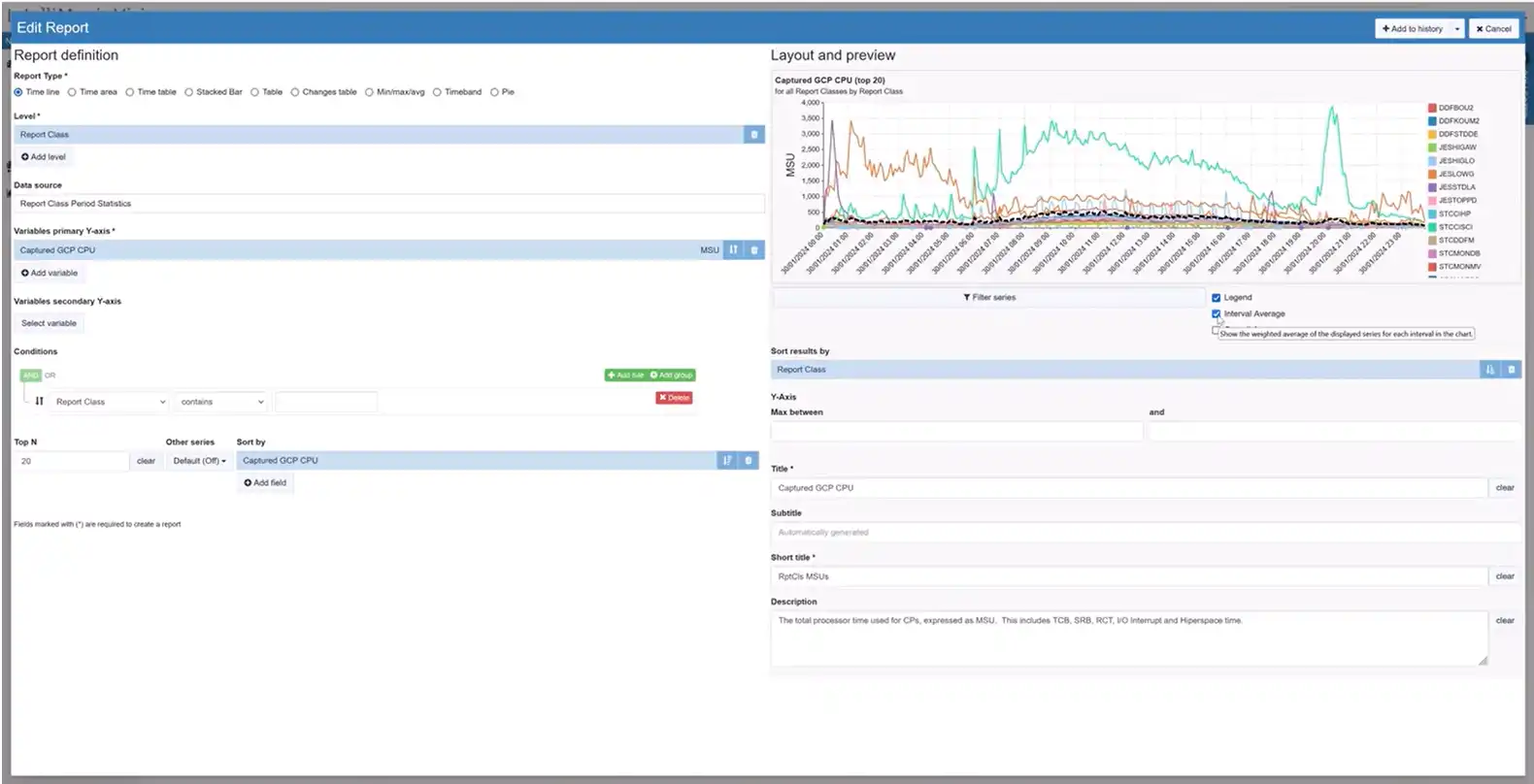
Long Term Reporting for MSU/MIPS Rates
Responding to customer requests, we have added long-term reporting for MSU (Million Service Units) or MIPS (Million Instructions Per Second) rates for service classes, service class periods, report classes, workloads, and every combination thereof. Users who have configured Applications based on Report Classes can also get the same visibility from the application perspective.
This enhancement empowers users to analyze CPU usage trends over time and make more informed decisions. The flexibility to view rates at different levels ensures a comprehensive perspective on system performance.
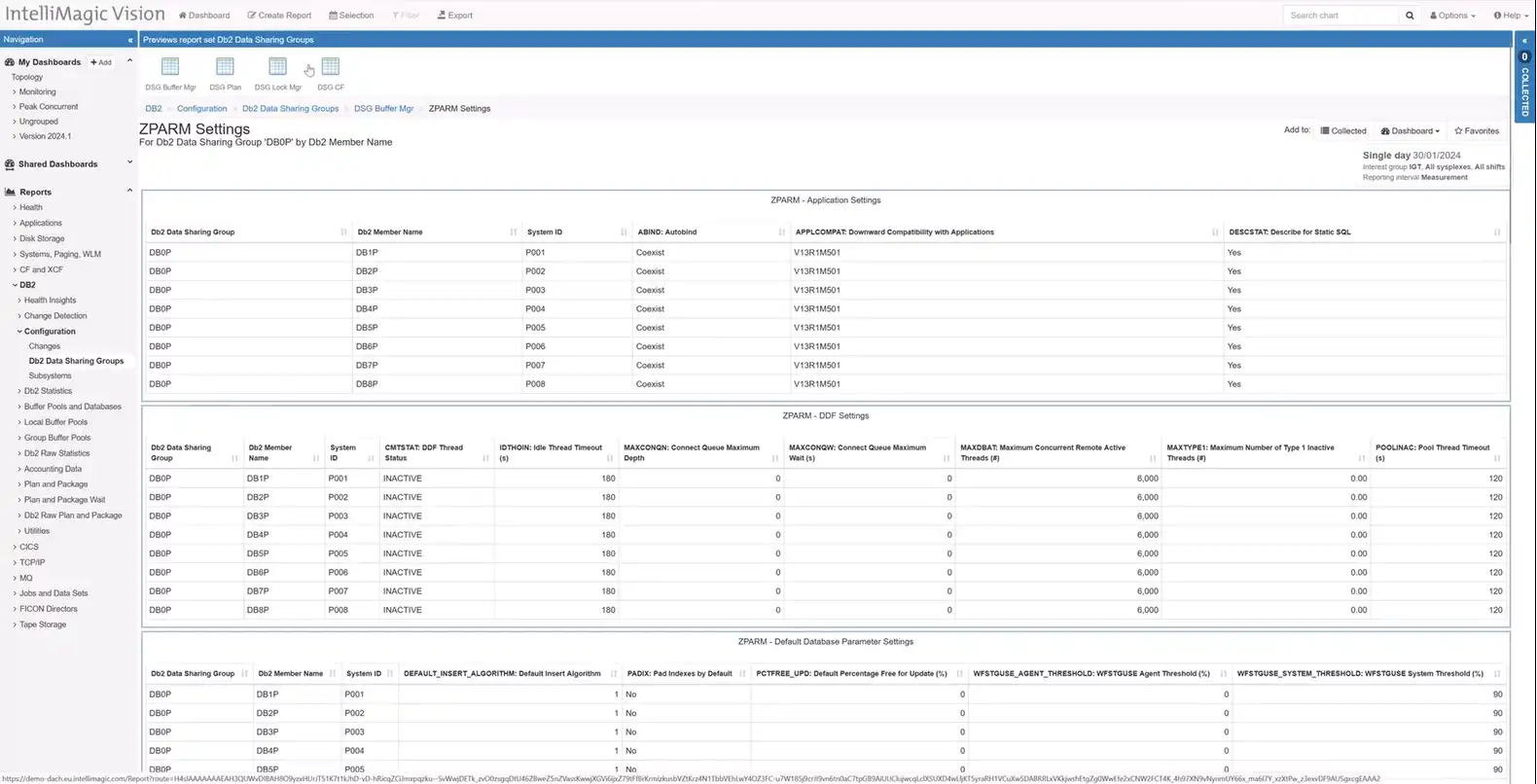
ZPARM Configurations for Db2
Managing Db2 configurations is made simpler with IntelliMagic Vision’s access to ZPARM settings. Users can easily navigate to ZPARM configurations from Db2 Data Sharing Groups, with focused reports on Buffer Manager Data, Plan Data, Lock Manager Stats, and Coupling Facility Structure.
The reports not only provide current settings but also offer change reports, aiding in tracking configuration modifications. Organized in logical reports, users can effortlessly access the information they need to manage Db2 effectively.
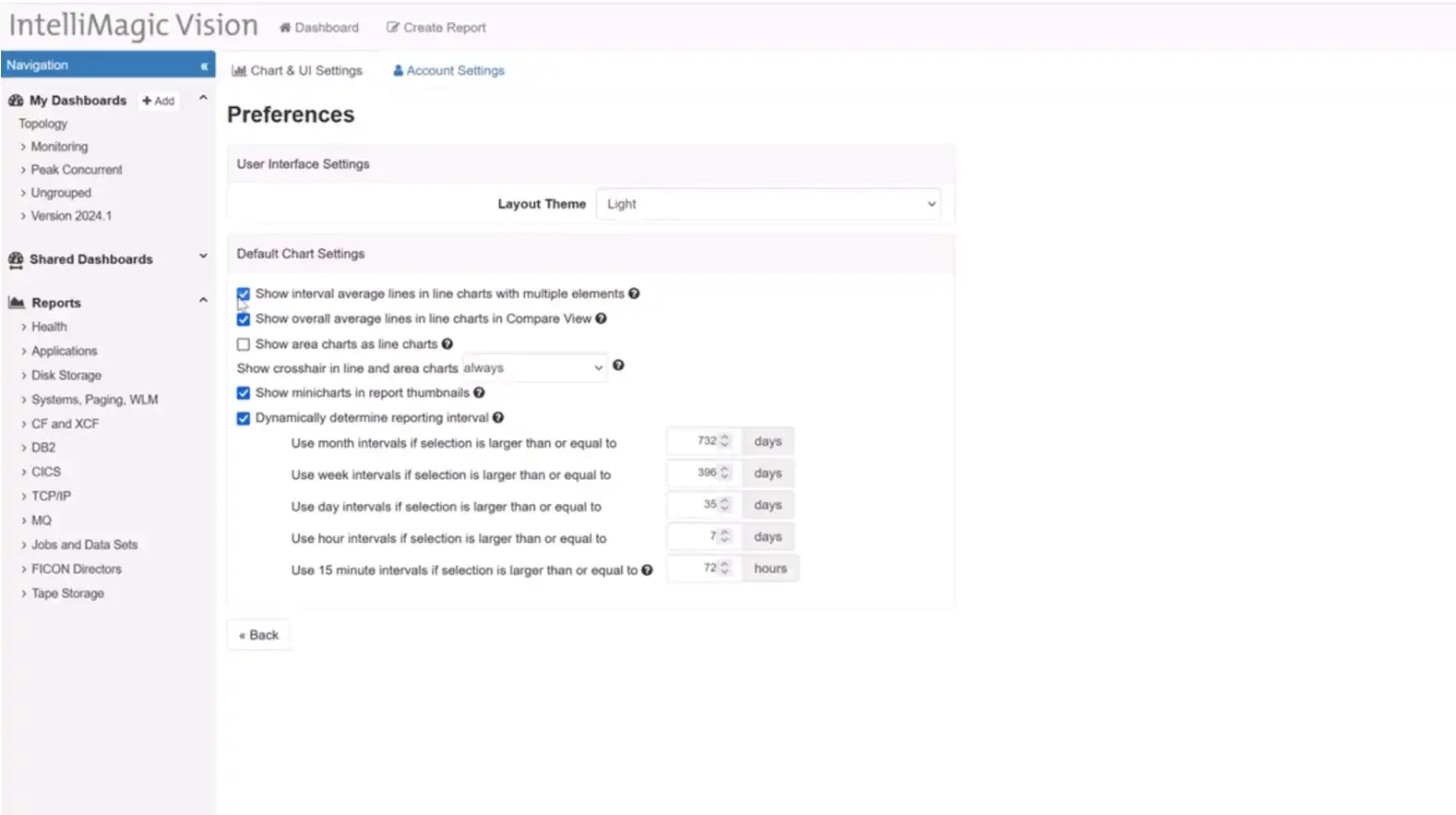
Interval Average Lines in Line Charts
IntelliMagic Vision 2024.01 introduces a change in our default settings based on user feedback. Now, new users will experience interval average lines turned off by default in line charts with multiple elements. This adjustment aligns with popular preferences, allowing users to choose when to display interval average lines, enhancing customization and user experience.
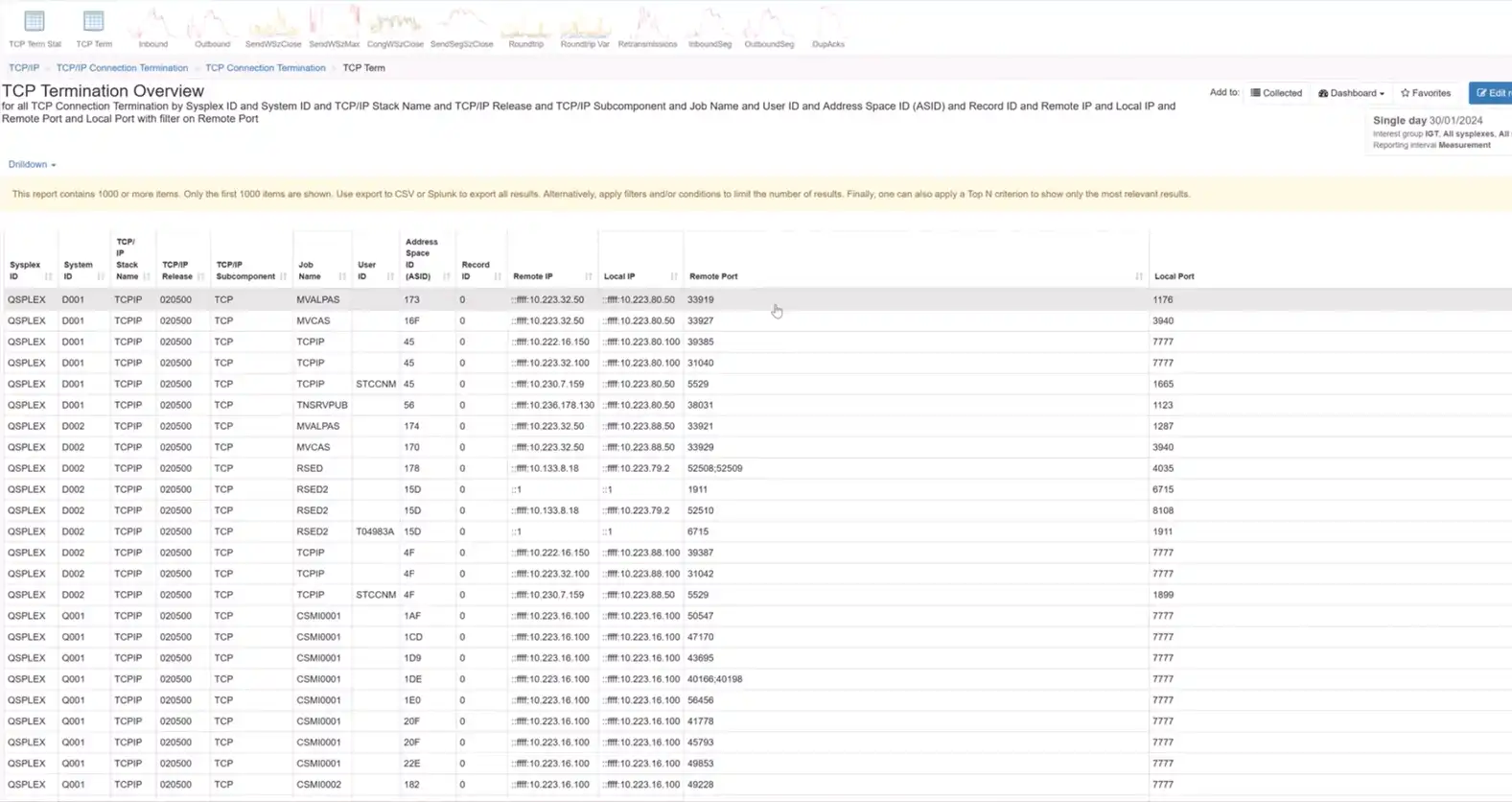
Enhancements in TCP/IP Communication Records
Validating security controls is made more robust with IntelliMagic Vision’s improvements in TCP/IP communication records. The SMF 119 subtype 12 records, widely used for security validation, are now complemented by an enhanced TCP Connection Termination report. This report showcases local and server IP addresses, server-side ports, and associated job names, facilitating easy identification of potentially risky port usage.
Other Updates in 2024.1
To see the full list of releases and updates in IntelliMagic Vision 2024.1, please refer to the Release Notes.
If you have feedback or feature requests, reach out to your technical account owner or contact us here. You can also sign up for our newsletter to always stay up to date with the latest releases, tips, content, and events.
Stay tuned for more updates in the next release!
You Might Also Be Interested In:
News
What's New with IntelliMagic Vision for z/OS? 2024.2
February 26, 2024 | This month we've introduced changes to the presentation of Db2, CICS, and MQ variables from rates to counts, updates to Key Processor Configuration, and the inclusion of new report sets for CICS Transaction Event Counts.
Webinar
A Mainframe Roundtable: The Leaders | IntelliMagic zAcademy
Join industry leaders as they discuss the evolution of mainframes, sharing personal experiences, challenges, and future insights, along with practical advice from their careers in the Z ecosystem.
Webinar
Challenging the Skills Gap – The Next Generation Mainframers | IntelliMagic zAcademy
Hear from these young mainframe professionals on why they chose this career path and why they reject the notion that mainframes are obsolete.
Book a Demo or Connect With an Expert
Discuss your technical or sales-related questions with our mainframe experts today
Top ‘IntelliMagic zAcademy’ Webinars of 2023
As year-end approaches I wanted to continue the tradition of looking back on the IntelliMagic zAcademy webinars that resonated most with our mainframe audience.
Since 2020, IntelliMagic zAcademy has offered free, educational z/OS webinars to the mainframe community. In 2023, we reached our 50th zAcademy webinar and covered topics from Mainframe Cost Savings to extracting insights from MQ data, mainframe security through zERT, application performance, and much more. But a top-5 countdown list can only have five.
The Top 5 IntelliMagic zAcademy webinars of 2023, as determined by total registration and attendance numbers, are:
(Honorable Mention) Metro Global Mirror (MGM) Monitoring in GDPS Sites
Okay, I’m going to cheat just a little here. Just narrowly escaping the top 5, was this session where IBM legend Joe Hyde offered practical advice on monitoring the Recovery Point Objective (RPO) and the factors influencing it.
While GDPS automation provides local storage resiliency and remote failover capabilities, it is the customer’s responsibility to supply adequate hardware infrastructure aligned with their business needs, especially concerning data recency at the remote site in case of a failure.
By monitoring performance data, participants can gain assurance that business requirements are met and can proactively make changes if issues arise, ensuring a resilient and optimized IT infrastructure.
#5) How Mainframe Performance Teams are Solving Their Skills Gap Challenges
Kicking off the actual top 5 list is a webinar that covered a topic on everyone’s mind: the mainframe skills gap. In this webinar, Brent Phillips and Todd Havekost discussed how several mainframe sites are addressing the imminent retirement of experienced mainframe personnel.
This recording is highly recommended for any and all sites experiencing the skills gap or trying to proactively avoid it.
#4) Where Are All The Performance Analysts? – A Mainframe Roundtable
Launching our foray into the ’roundtable’ business, our 4th most attended session of the year was truly a meeting of the minds. With the likes of Martin Packer, Frank Kyne, Dave Hutton, and Jim Horne joining IntelliMagic’s own Todd Havekost and John Baker, these guys touched on everything performance – from costs, to labor, how to speak to management, AI, and much more.
Getting a group of experts like this on a single call is truly and honor and spectacle so if you haven’t already, I highly recommend viewing or listening to the recording.
#3) From Taped Walls to Your PC: z/OS Configuration Made Simple
z/OS Performance and Configuration data is very useful for understanding complicated issues and solving problems, but sometimes it is hard to fully grasp what the data is showing us. Traditional methods of viewing and understanding our z/OS configuration often involved physically taping the mapped-out-topology to office walls – something not feasible or desirable in today’s massively complex environments.
In our third most viewed webinar of the year, John Ticic and Todd Havekost discussed and demonstrated a breakthrough new method of interpreting and interacting with the LPAR, FICON, and Sysplex topologies.
#2) Oh Where Performance Will Take You: A Mainframe Roundtable
Our second ever zAcademy Roundtable hosted the likes of Cheryl Watson and Craig Walters amongst a rockstar group of performance and capacity analysts. So there’s no surprise that this comes in at #2 on our list.
Moderated again by John Baker, this roundtable event explored the journey of several renown mainframe performance analysts and offered insights and perspectives on timeless topics.
Panelists included:
- Cheryl Watson, Watson & Walker
- Craig Walters, IBM
- Dave Barry, UPS
- Jon Ulrich, HCSC
- Todd Havekost, IntelliMagic
#1) Unraveling the z16: Understanding the Virtual Cache Architecture and Real-World Performance
By and far the #1 most viewed zAcademy session of 2023 (and all time) was this session presented by John Baker and Todd Havekost.
During this ground-breaking discussion, John and Todd discussed the revolutionary changes brought about by the z16 processor architecture, and walked through the results of numerous recent upgrade analysis’ with surprising results.
With the introduction of virtual cache at levels 2, 3, and 4, the z16 marks the most substantial transformation in the z processor architecture since the z13. For any site who is considering migrating to the z16 (or already has), this is truly a can’t miss session on what results you can likely expect and how you can verify you received (and are receiving) the expected results.
Looking Towards 2024
If you haven’t yet watched any of the live sessions or recordings of this year’s zAcademy sessions, or if you’re a super-learner that signs up for every session, remember that all zAcademy webinars and recordings – past and future – can be accessed at www.intellimagic.com/zacademy/
IntelliMagic zAcademy will continue into 2024 with exciting insights and deep dives into several new areas of the z/OS mainframe. If you have a favorite session you want to tell us about, have questions about any of the material you saw, or if you have a recommendation on a topic you want us to cover in the future, send us a note at info@intellimagic.com, and we’ll get back to you!
Thanks for watching – tune in next year!
This article's author
Share this blog
Related Resources
News
What's New with IntelliMagic Vision for z/OS? 2024.2
February 26, 2024 | This month we've introduced changes to the presentation of Db2, CICS, and MQ variables from rates to counts, updates to Key Processor Configuration, and the inclusion of new report sets for CICS Transaction Event Counts.
Webinar
A Mainframe Roundtable: The Leaders | IntelliMagic zAcademy
Join industry leaders as they discuss the evolution of mainframes, sharing personal experiences, challenges, and future insights, along with practical advice from their careers in the Z ecosystem.
Webinar
Challenging the Skills Gap – The Next Generation Mainframers | IntelliMagic zAcademy
Hear from these young mainframe professionals on why they chose this career path and why they reject the notion that mainframes are obsolete.
Book a Demo or Connect With an Expert
Discuss your technical or sales-related questions with our mainframe experts today
Banco do Brasil Ensures Availability for Billions of Daily Transactions with IntelliMagic Vision
Company Overview
Banco do Brasil, with over 87,000 employees, 5,000 branches, and 81 million customers, is one of the largest banks in the world, processing over 15 billion transactions per day. Headquartered in Brasilia, Brazil, Banco do Brasil provides commercial and government services as well as a large variety of consumer services, including bill payment services, ATM loans, and checking, savings, and investment accounts.
 > 87,000 employees > 87,000 employees |
 > 5,000 branches > 5,000 branches |
 > 81 millions of customers > 81 millions of customers |
 > 15 billion transaction per day > 15 billion transaction per day |
The Challenge
As the second largest financial services company in Latin America, Banco do Brasil has one of the largest and most complex IT infrastructure environments in the world. As a publicly owned bank with billions of daily transactions and millions of customers, there is no margin for system downtime or application disruptions.
Previous solutions to manage performance and conduct capacity planning were cumbersome, slow, required manual coding, and were not interactive or easy to train new hires on. They needed a solution that would allow them to keep up with modern demands, rising transactions, and expanding data volumes.
The Solution
For more than a decade, Banco do Brasil has used IntelliMagic Vision to monitor and manage the performance and availability of their entire end-to-end z/OS and SAN infrastructure environments.
“We use IntelliMagic Vision for z/OS on a daily basis to investigate bottlenecks and analyze performance problems. We also use IntelliMagic Vision for z/OS to improve our system and storage designs and better understand our environment. IntelliMagic Vision has been extremely helpful in post-mortem analysis.”
– Fabio Pereira, Banco do Brasil, Storage Manager
Banco do Brasil uses IntelliMagic Vision for z/OS Systems, CICS, Db2, Disk & Replication, Virtual Tape, as well as SAN Storage, Fabric, and VMware.
IntelliMagic Vision also met the organization’s core requirements with its:
- Built-in health insights to proactively avoid disruptions
- Extensive drill down capabilities
- Code free report builder
- Capacity Planning
- Intuitive graphical user interface
Business Results
IntelliMagic Vision enabled Banco do Brasil to streamline its performance management and capacity planning and enhance its overall business operations.
With IntelliMagic Vision, Banco do Brasil was able to:
- Proactively highlight and prevent potential availability issues
- Eliminate redundant tooling and use a single interface across infrastructure areas
- Reduce mean-time-to-resolution for problems
- Enhance communication and cooperation amongst different teams
To learn more about how Banco do Brasil uses IntelliMagic Vision, view the full review on TrustRadius.
Book a Demo or Connect With an Expert
Discuss your technical or sales-related questions with our mainframe experts today
Benefits of Analysis Across SMF Data Types
Escaping Data Silos Within SMF Data Types
Mainframe performance analysts rely heavily on the great insights provided by SMF measurement data into each component of the z/OS ecosystem. While there is extensive interaction and interdependence across many of the z/OS components, analysis of various SMF data types often relies on tooling that is unique to each data type.
Unfortunately, this has formed a barrier to collaborating on performance analysis across disciplines.
This article will show examples of how performance analysts can become more effective through having visibility into multiple types of SMF data.
Examples cited in this article are based on SMF data from:
- WLM and CICS
- Address Space and Db2 Accounting
- CICS and Db2
- MQ and CICS
Hopefully these scenarios will stimulate your thinking to identify many other situations where analysis performed by your teams can benefit from collaboration and using SMF data across disciplines.
No matter which subsystem you are primarily responsible for, we hope this article will help you blur the boundaries between the SMF ‘silos’ for each product.
IntelliMagic highly recommends subscribing to the quarterly Watson Walker Tuning Letter for the best z/OS technical articles in the industry.
A Performance Analyst’s Guide to Mainframe zERT Analysis | IntelliMagic zAcademy
The mainframe is one of the most secure computing platforms in the world – offering best-of-class encryption on top of its blistering performance capabilities. But that doesn’t mean you don’t need to manage your network encryption carefully.
Regardless of the hat you wear: Performance, Capacity, Systems; everyone has some responsibility for security. Who gets the ‘honor’ of the next audit? How do we make sure the next security improvement doesn’t wreck performance with assumptions about processor configurations?
A security analyst role in the mainframe world likely also needs to understand the other components, too. Do you have something that helps you connect the dots? This webinar will introduce you to some of the ways to identify security risks and issues within network traffic and provide actionable strategies and recommendations to ensure they don’t appear at your site or cause an unplanned resource demand increase.
Watch this webinar recording to learn strategies for:
- Identifying and addressing any encryption gaps you may currently have
- Providing security-related management reporting
- Improving collaboration with Integrated reporting on multiple SMF record types
- Measuring the CPU impact of technology differences
Translating Application Performance Data into Business Outcomes on z/OS | IntelliMagic zAcademy
Get Notified of Upcoming Webinars
In a world where applications are at the forefront, it can be difficult to know which applications are critical to your business and how to protect them. The z/OS system manages a large number of applications, some of which are vital to the success of your business.
Performance analysts need to understand both the business and operational aspects of all applications to ensure z/OS manages them optimally. A key to a performance analyst’s effectiveness is to be able to translate what the business requires of the z/OS system and what the performance data is telling those in charge of the business.
In this webinar, we explore practical steps for identifying and prioritizing your business-critical applications, and how to optimize and report on their performance. We cover key considerations, such as CPU and Disk performance, defining service classes, and spotting relevant changes in the midst of overwhelming data.
You learn:
- How to identify and prioritize your “most loved” business-critical applications
- How to examine all aspects affecting the applications, including CICS, Db2, and Systems components
- Techniques for ensuring service classes are defined correctly
- Ways to spot and identify relevant changes through data analysis
- Strategies for protecting and reporting on performance
- Reporting the health of applications to those not close to the operation of z/OS
Watch this informative and engaging webinar to learn how to cut through the noise and ensure your mission-critical applications are functioning optimally on z/OS.
Sign Up for our Newsletter
Subscribe to our monthly newsletter and receive great quality content in your inbox on:
- performance tips and best practices from industry experts
- tutorials and walkthroughs
- latest industry news
- valuable resources
- upcoming events
- and more
Complete the Form to Sign Up
Related Resources
News
What's New with IntelliMagic Vision for z/OS? 2024.2
February 26, 2024 | This month we've introduced changes to the presentation of Db2, CICS, and MQ variables from rates to counts, updates to Key Processor Configuration, and the inclusion of new report sets for CICS Transaction Event Counts.
Webinar
A Mainframe Roundtable: The Leaders | IntelliMagic zAcademy
Join industry leaders as they discuss the evolution of mainframes, sharing personal experiences, challenges, and future insights, along with practical advice from their careers in the Z ecosystem.
Webinar
Challenging the Skills Gap – The Next Generation Mainframers | IntelliMagic zAcademy
Hear from these young mainframe professionals on why they chose this career path and why they reject the notion that mainframes are obsolete.
Book a Demo or Connect With an Expert
Discuss your technical or sales-related questions with our mainframe experts today
IntelliMagic and Watson & Walker: Partners in Mainframe Optimization
Company Overview
Watson & Walker is a vendor-independent mainframe consultancy firm that provides practical mainframe performance and measurement advice. Founded by Cheryl Watson and Tom Walker in 1991, the Watson & Walker team is one of the best-known and respected z/OS performance and measurement advisory groups in the world. Cheryl Watson’s Tuning Letter, named after the co-founder and mainframe legend, is the most comprehensive body of practical and impartial z/OS tuning and measurement advice ever published.
The Challenge
As the very nature of their business, Watson & Walker provides consulting services for clients spanning the globe, but their existing method of SMF performance analysis required manual coding, wasn’t dynamic or interactive, and couldn’t keep up with the pace of the demands from their work.
Watson & Walker needed a way to quickly navigate and analyze the mainframe environment in order find performance optimization and cost reducing opportunities for their clients.
Watson & Walker embarked on a research project to find the perfect SMF performance analysis tool available on the market. To meet Watson & Walker’s strict criteria, their chosen solution needed to:
- Be powerful, robust, and interactive
- Save time conducting analysis
- Offer great customer support
- Be up to date on the latest mainframe technology and metrics
The Solution
After analyzing the solutions on the market and consulting with customers from each of the solutions, Watson & Walker decided upon IntelliMagic Vision for z/OS. Since 2016, Watson & Walker has used IntelliMagic Vision for z/OS with their consulting efforts when helping customers and generating reports.
“At the conclusion of our research, we found that IntelliMagic Vision, without a doubt, is heads and shoulders above anything else. We wouldn’t go anywhere without IntelliMagic Vision; it is powerful, easy to use, and is now a vital part of our toolkit when creating presentations, classes, Tuning Letters, or customer reports.”
– Cheryl Watson, CEO and Founder, Watson & Walker
Business Results
The partnership between Watson & Walker and IntelliMagic allows mainframe customers to benefit from IntelliMagic Vision’s built-in intelligence and Watson & Walker’s unrivaled services.
Using IntelliMagic Vision, Watson and Walker was able to:
- save significant time by applying their experience to the analysis, not in trying to extract and organize the information out of SMF
- more quickly and accurately spot tuning opportunities for cost reduction and performance optimization
- take advantage of the built-in health insights to identify warnings and issues prior to their deep-dive analysis
“What I liked most about IntelliMagic Vision was its automatic identifying of the key performance indicators, the KPIs, and the ability to drill down. The whole idea of looking at this boundless information from SMF, is that you don’t want to spend time looking at all that information. All you want to know is, is everything okay or is something wrong? So the ability to drill down, look at only one of the items instead of multiple is pretty powerful and takes no programming.”
Related Resources
News
What's New with IntelliMagic Vision for z/OS? 2024.2
February 26, 2024 | This month we've introduced changes to the presentation of Db2, CICS, and MQ variables from rates to counts, updates to Key Processor Configuration, and the inclusion of new report sets for CICS Transaction Event Counts.
Webinar
A Mainframe Roundtable: The Leaders | IntelliMagic zAcademy
Join industry leaders as they discuss the evolution of mainframes, sharing personal experiences, challenges, and future insights, along with practical advice from their careers in the Z ecosystem.
Webinar
Challenging the Skills Gap – The Next Generation Mainframers | IntelliMagic zAcademy
Hear from these young mainframe professionals on why they chose this career path and why they reject the notion that mainframes are obsolete.
Book a Demo or Connect With an Expert
Discuss your technical or sales-related questions with our mainframe experts today
Closing the Gap on Mainframe Application Profiling | IntelliMagic zAcademy
In today’s age of ‘app’ proliferation and data overload in most areas of z/OS infrastructure performance, one would think we would have access to endless statistics on application behavior. While this is largely true in the distributed space, it remains an elusive goal in our beloved mainframe.
The simple fact is distributed application programmers and mainframe system folks speak very different languages (when they speak to each other at all). DDF transactions don’t ‘look’ like CICS transactions – but they are both important to the business.
In this session, John Baker and Gabe Tully try to break down the barriers between z/OS and distributed systems and communicate specific methods both sides can use to classify workloads properly.
Leveraging zERT and Other SMF Data to Manage and Optimize Network Encryption | IntelliMagic zAcademy
Given the importance of security in today’s world, managing network encryption is a critical requirement for almost every z/OS environment. Beginning with z/OS 2.3, IBM provides the capability to have an entirely new level of visibility into the encryption status of all network traffic to and from your z/OS systems. This is enabled through z/OS Encryption Readiness Technology (zERT), which makes this data available in SMF 119 records.
This zERT data can be of great benefit to network security teams who are responsible to ensure that transmitted data is encrypted in accordance with corporate standards. But sites typically have alternatives when choosing between encryption methods, some of which drive significantly more CPU overhead than others. This heightens the importance of having clear visibility into CPU data to help identify the most cost-effective approach.
Watch this session to learn more about the value provided by zERT and other SMF data:
- To identify and address any encryption gaps you may currently have
- To provide the reporting required by auditors and compliance officers
- To enhance analysis by classifying data into distinct traffic classes
- To measure the CPU impact of alternative encryption methods using several real-life examples
- To help your organization answer other non-security questions.
You may also find that using this data can help your organization answer other non-security questions.
z/OS Health Insights, Ratings, and Thresholds with IntelliMagic Vision
Learn how to automatically highlight any developing problems in your z/OS infrastructure
This white paper demonstrates how IntelliMagic Vision can be used to obtain intelligence about threats in your z/OS infrastructure that are likely to lead to service disruptions for your users and applications or replication health.
The Health Insights will automatically highlight any developing problems. You can configure the thresholds to match the needs of your workload, such that IntelliMagic Vision will become more and more intelligent about your environment as you continue to use and configure the product.
IntelliMagic Vision provides Health Insights for:
- Disk Storage Systems
- Storage Groups
- System and Workload Manager
- Log Streams
- Coupling Facility
- Cross-system Coupling Facility (XCF)
- Db2
- CICS
- MQ
- TCP/IP
- FICON and Channels
- TS7700
Gain insight into how these Health Insights and over 2000 charts can help you identify and solve performance issues.
To download this white paper, please complete the form to the right, and we will send the file to your email.
Overall z/OS Performance & Health Status
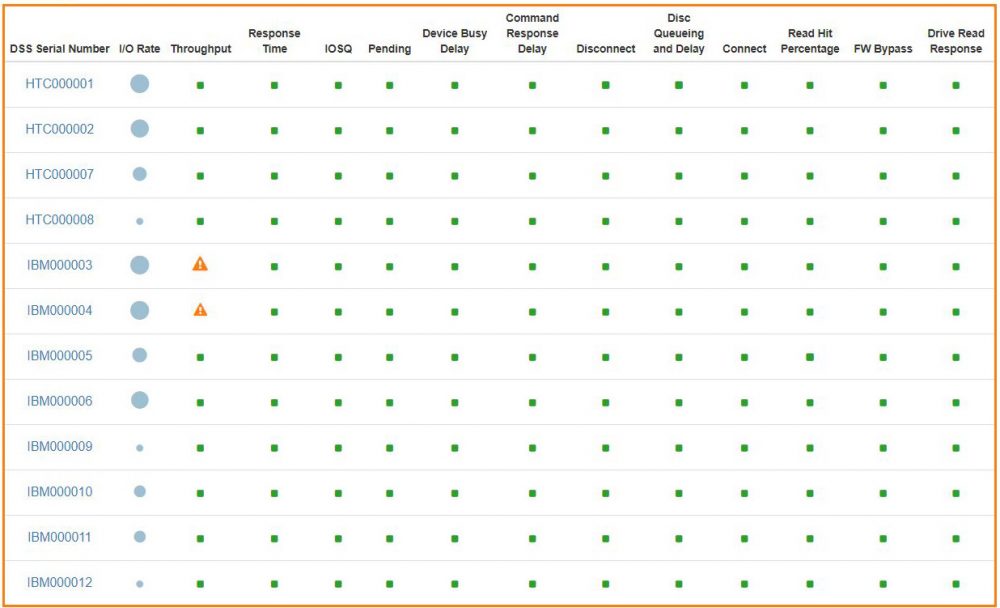
The goal of IntelliMagic Vision is to identify potential issues before they impact applications. This is achieved by an intelligent rating system where workload measurements are combined and compared with the capabilities of the systems. The resulting ratings are shown in health insights charts that represent the health of your entire end-to-end z/OS infrastructure.
The health insight reports indicates infrastructure health by showing the key ratings for each part of the environment. Ratings are based on the analysis of thousands of underlying data points, making the health insight charts a very dense summary of hundreds of charts. The result is that issues and risks are flagged proactively before application performance degrades.
The dashboards show the summary; drill-downs allow you to explore details. The color and size of these bubbles show the ratings for the underlying metrics:
- a green icon indicates a healthy situation
- a yellow icon indicates that a problem is developing
- red icons flag more severe risks or issues
With these visual cues, it is extremely easy to see the health status of the entire environment at a glance.
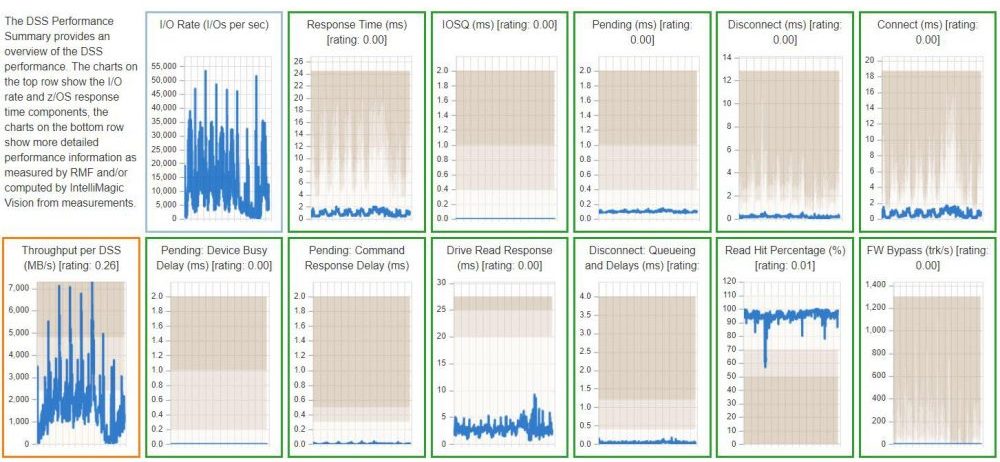
Investigate Performance Details
The health insights chart shown above provides the most compact view, but the rating is based on a very detailed level of analysis. To get more information about an issue, you can click on any icon to get to to the next level of detail. The icons are replaced by several related mini charts that show the metrics over time, as well as the rating and threshold values.
Root Cause Analysis
When the chart shows a problem, you can click on one of the mini charts to get a full version of the chart, which also contains an explanation of the metric and thresholds, as well as recommendations on what could be done to address the issue. The border of the charts is colored in the same way as the health insights chart:
- a green border means a healthy metric
- yellow is for early warning
- red indicates a larger issue
Each individual chart contains multiple drill-down options to go to the deepest level of detail in any direction, for example to find the individual RAID array that was so busy that it caused a large red circle for drive response time in the highest level dashboard.
Customizability
There are thousands of pre-defined charts and reports available in IntelliMagic Vision, grouped into logical sets. If you are interested in showing a combination of metrics or filters that is not available out of the box, you can customize the charts, or define your own from scratch and add it to your favorite chart set. The thresholds that are used in the rating system are also customizable to fit your situation.
All charts and reports can be exported to CSV, HTML, PDF, PowerPoint and Splunk.
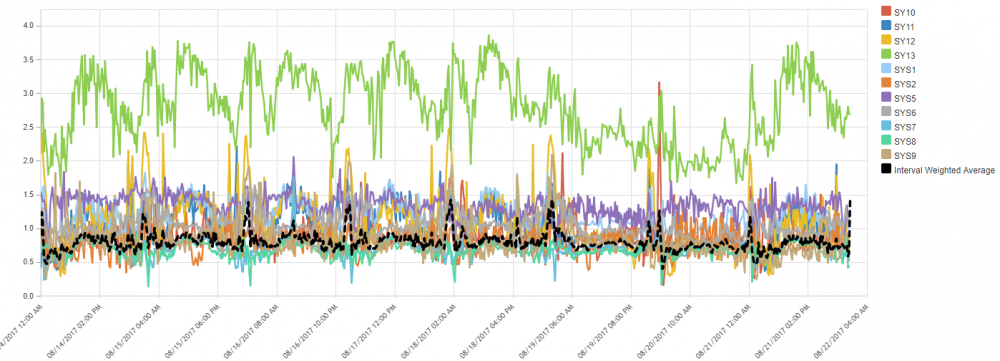
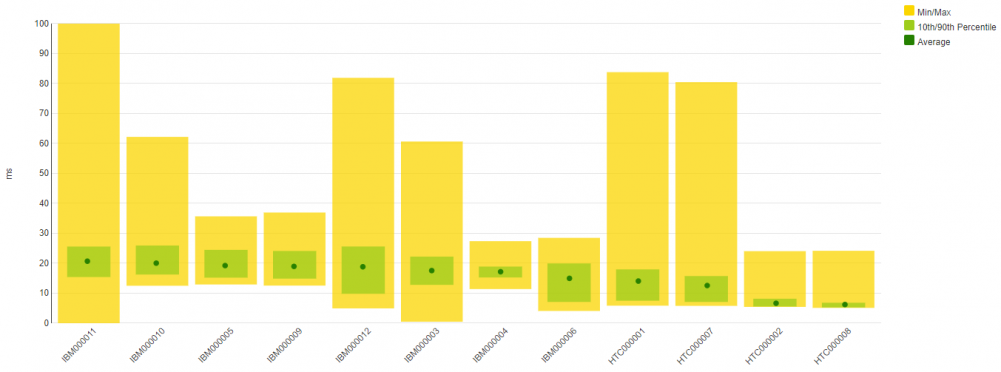
Balance Charts
Many metrics are best shown as line or area charts, but some values are better looked at in a different fashion. The variance chart, for instance, is a great way to show (im)balance. In the example below, you see the FICON throughput per port.
- a green dot indicates average throughput for the port
- a green rectangle that shows the standard deviation
- a yellow area that shows the minimum and maximum value over the entire period








 “At the conclusion of our research, we found that IntelliMagic Vision, without a doubt, is heads and shoulders above anything else. We wouldn’t go anywhere without IntelliMagic Vision; it is powerful, easy to use, and is now a vital part of our toolkit when creating presentations, classes, Tuning Letters, or customer reports.”
“At the conclusion of our research, we found that IntelliMagic Vision, without a doubt, is heads and shoulders above anything else. We wouldn’t go anywhere without IntelliMagic Vision; it is powerful, easy to use, and is now a vital part of our toolkit when creating presentations, classes, Tuning Letters, or customer reports.”